Get a 360 degree view of your data with an integration between dataBelt® and any cyber security tool
Data is an organisation's crucial resource, its life blood, its reason for being. Thus if data is recognised as a critical resource, then it needs to be managed. It needs to be secure, clean, compliant.
The integration between a cyber security tool and dataBelt® brings together two complementary products - the cyber security tool for in-depth analysis of threats to your assets, and dataBelt® for deep understanding of your data.
DataBelt® carries its own cyber security feed, but where organisations have already invested in an enterprise cyber security tool, dataBelt can integrate with it seamlessly.
Bringing two enterprise tools together ensures both your security operations centre (SOC) and risk and compliance teams are aligned to any abnormal behaviours within your organisation. Cyber security tools monitor millions of pieces of data every second, and maintain tens of milllions of relationships between the data. dataBelt® ensures you know exactly what data you have, where and how it is stored, and to prioritise actions based on classification and value.
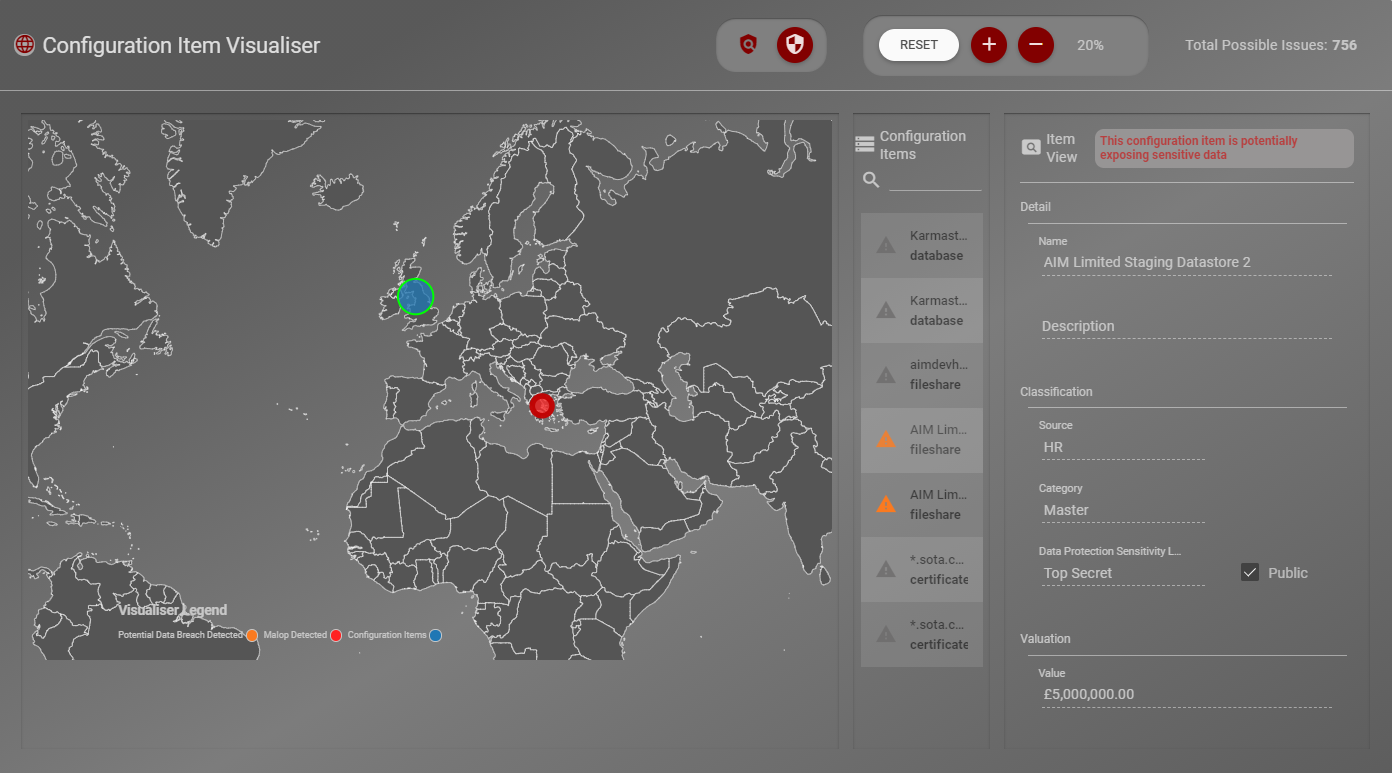
Cyber security tools and dataBelt® real-time analysis: Working together to safeguard your data
Know the status of your data at all times. DataBelt® links into your Configuration Management Database (CMDB) which allows the system to index all your organisation's configuration items (CIs). So when your company has a security incident / event, you know precisely what data is impacted and the sensitivity levels of that data. Understanding the data sensitivity during an incident is critical in assisting your security teams to prioritise the actions required for a successful outcome.